mirror of
https://github.com/funkypenguin/geek-cookbook/
synced 2025-12-25 15:41:40 +00:00
Update for leanpub preview
This commit is contained in:
@@ -15,7 +15,7 @@ This is the role of the OAuth proxy.
|
||||
When employing the **OAuth proxy** , the proxy sits in the middle of this transaction - traefik sends the web client to the OAuth proxy, the proxy authenticates the user against a 3rd-party source (_GitHub, Google, etc_), and then passes authenticated requests on to the web app in the container.
|
||||
|
||||
Illustrated below:
|
||||
![OAuth proxy]https://geek-cookbook.funkypenguin.co.nz/images/oauth_proxy.png)
|
||||
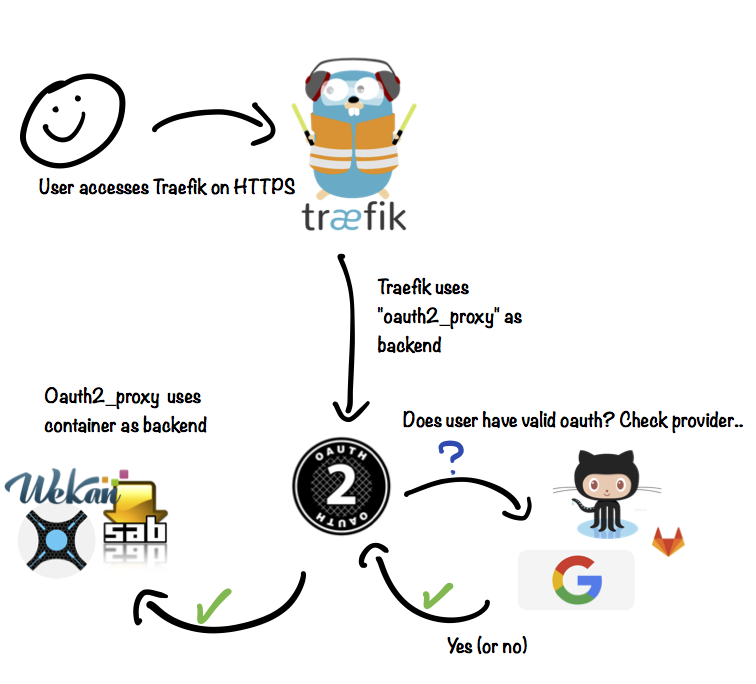
|
||||
|
||||
The advantage under this design is additional security. If I'm deploying a web app which I expect only myself to require access to, I'll put the oauth_proxy in front of it. The overhead is negligible, and the additional layer of security is well-worth it.
|
||||
|
||||
@@ -47,7 +47,7 @@ I created **/var/data/oauth_proxy/authenticated-emails.txt**, and add my own ema
|
||||
|
||||
### Configure stack
|
||||
|
||||
You'll need to define a service for the oauth_proxy in every stack which you want to protect. Here's an example from the [Wekan]https://geek-cookbook.funkypenguin.co.nz/recipes/wekan/) recipe:
|
||||
You'll need to define a service for the oauth_proxy in every stack which you want to protect. Here's an example from the [Wekan](https://geek-cookbook.funkypenguin.co.nz/recipes/wekan/) recipe:
|
||||
|
||||
```
|
||||
proxy:
|
||||
|
||||
Reference in New Issue
Block a user