mirror of
https://github.com/funkypenguin/geek-cookbook/
synced 2025-12-13 01:36:23 +00:00
Fix more broken links, add lazy-loading to images
This commit is contained in:
1
.gitignore
vendored
1
.gitignore
vendored
@@ -45,3 +45,4 @@ notes/
|
||||
ehthumbs.db
|
||||
Thumbs.db
|
||||
.venv
|
||||
venv
|
||||
|
||||
@@ -15,7 +15,7 @@ Sponsor [your chef](https://github.com/sponsors/funkypenguin) :heart:, or [join
|
||||
|
||||
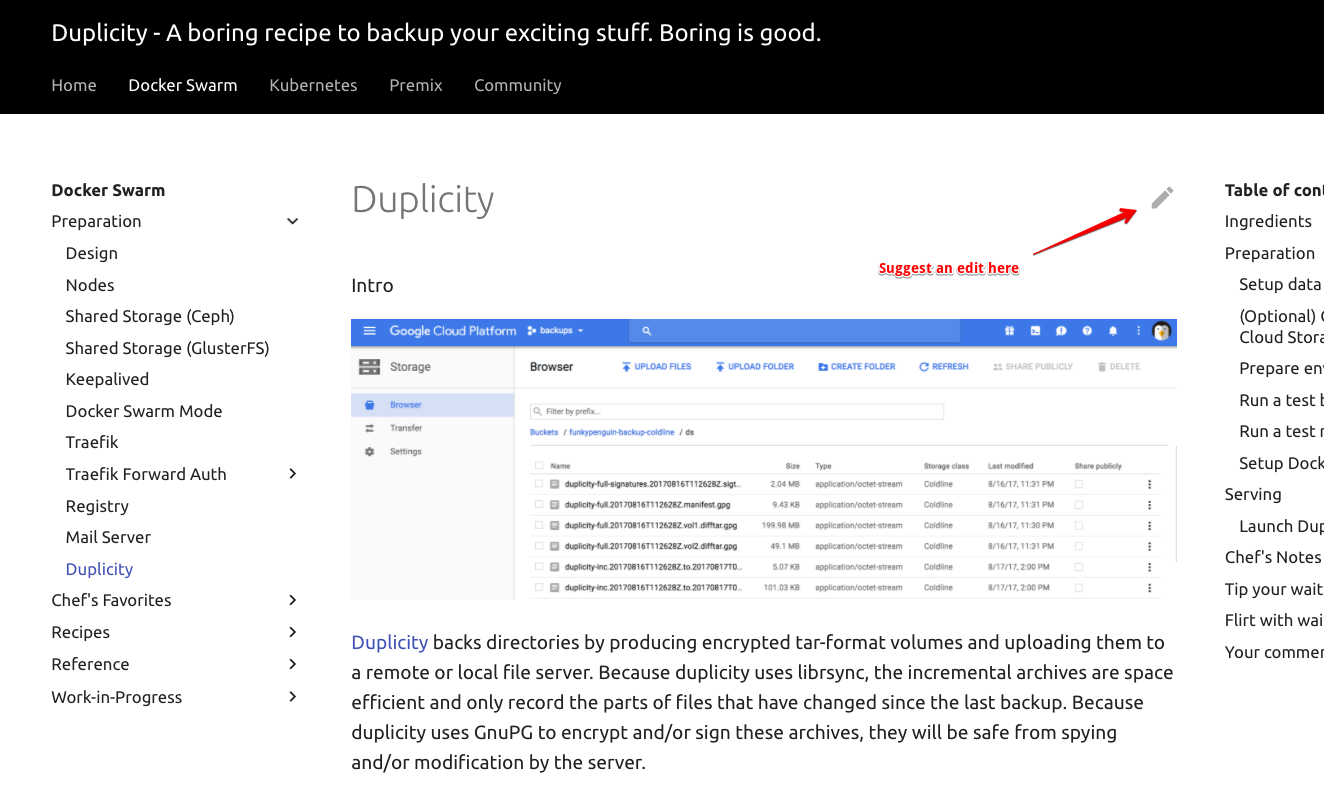
Found a typo / error in a recipe? Each recipe includes a link to make the fix, directly on GitHub:
|
||||
|
||||
|
||||
{ loading=lazy }
|
||||
|
||||
Click the link to edit the recipe in Markdown format, and save to create a pull request!
|
||||
|
||||
@@ -37,11 +37,11 @@ GitPod (free up to 50h/month) is by far the smoothest and most slick way to edi
|
||||
|
||||
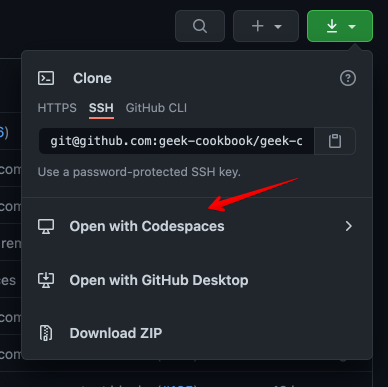
[GitHub Codespaces](https://github.com/features/codespaces) (_no longer free now that it's out of beta_) provides a browser-based VSCode interface, pre-configured for your development environment. For no-hassle contributions to the cookbook with realtime previews, visit the [repo](https://github.com/geek-cookbook/geek-cookbook), and when clicking the download button (*where you're usually get the URL to clone a repo*), click on "**Open with CodeSpaces**" instead:
|
||||
|
||||
|
||||
{ loading=lazy }
|
||||
|
||||
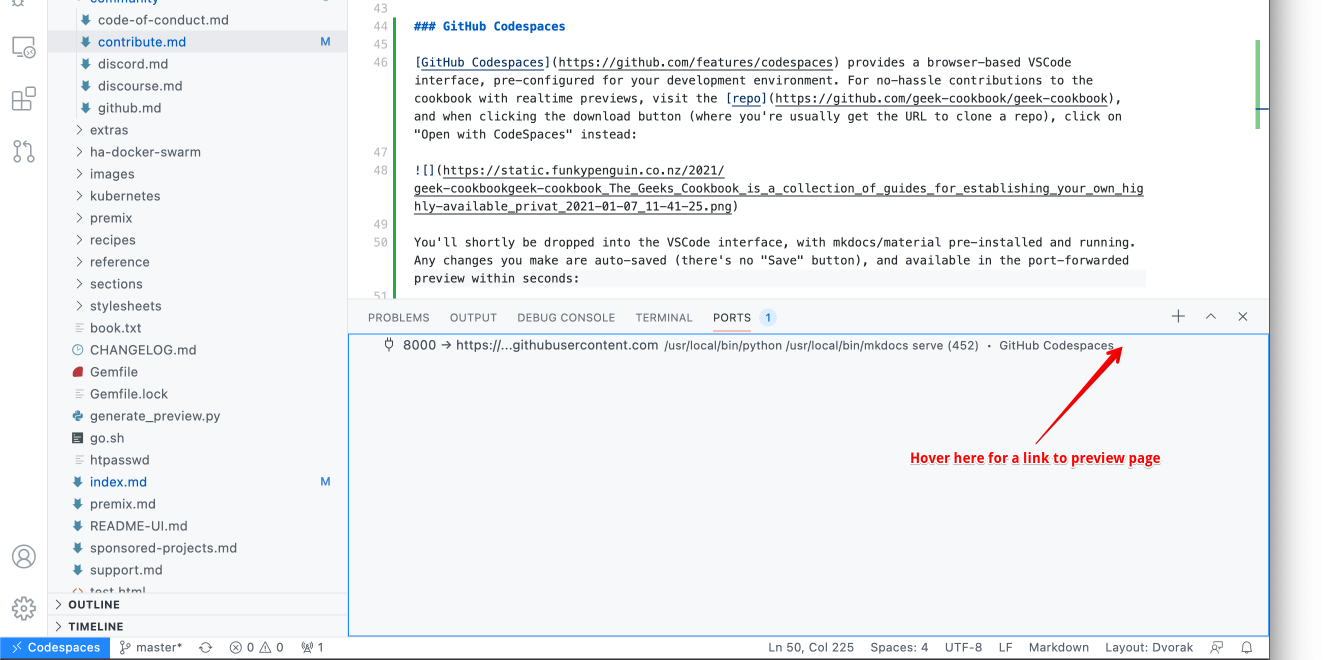
You'll shortly be dropped into the VSCode interface, with mkdocs/material pre-installed and running. Any changes you make are auto-saved (*there's no "Save" button*), and available in the port-forwarded preview within seconds:
|
||||
|
||||
|
||||
{ loading=lazy }
|
||||
|
||||
Once happy with your changes, drive VSCode as normal to create a branch, commit, push, and create a pull request. You can also abandon the browser window at any time, and return later to pick up where you left off (*even on a different device!*)
|
||||
|
||||
@@ -59,7 +59,7 @@ The process is basically:
|
||||
8. Create a pull request via the GitHub UI
|
||||
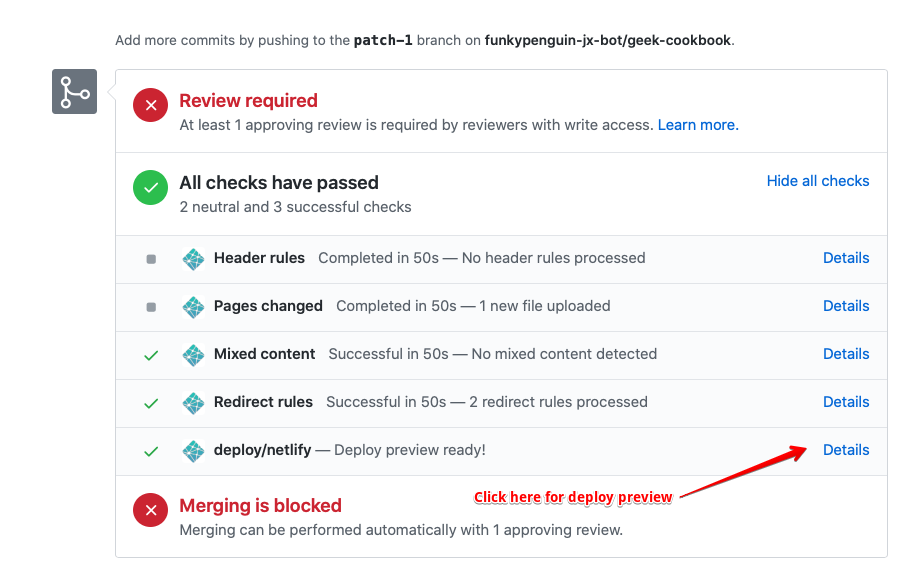
9. The pull request will trigger the creation of a preview environment, as illustrated below. Use the deploy preview to confirm that your recipe is as tasty as possible!
|
||||
|
||||
|
||||
{ loading=lazy }
|
||||
|
||||
## Contributing skillz 💪
|
||||
|
||||
|
||||
@@ -15,6 +15,6 @@ With the goal of creating a safe and inclusive community, we've adopted the [Con
|
||||
|
||||
To report a violation of our code of conduct in our subreddit, use the "Report" button as illustrated below:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
The reported message will be highlighted to moderators, who will address the issue as detailed in the [enforcement guidelines](/community/code-of-conduct/#enforcement-guidelines).
|
||||
|
||||
@@ -7,7 +7,7 @@ description: Authelia is an open-source authentication and authorization server
|
||||
|
||||
[Authelia](https://github.com/authelia/authelia) is an open-source authentication and authorization server providing 2-factor authentication and single sign-on (SSO) for your applications via a web portal. It acts as a companion of reverse proxies like Nginx, Traefik, or HAProxy to let them know whether queries should pass through. Unauthenticated users are redirected to Authelia Sign-in portal instead.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Features include
|
||||
|
||||
@@ -245,7 +245,7 @@ Launch the Authelia stack by running ```docker stack deploy authelia -c <path -t
|
||||
|
||||
To test the service works successfully. Try to access a service that you had added the middleware label to. If it works successfully you will be presented with a login screen
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[^1]: The inclusion of Authelia was due to the efforts of @bencey in Discord (Thanks Ben!)
|
||||
|
||||
|
||||
@@ -59,7 +59,7 @@ Assuming a 3-node configuration, under normal circumstances the following is ill
|
||||
* The **traefik** service (*in swarm mode*) receives incoming requests (*on HTTP and HTTPS*), and forwards them to individual containers. Traefik knows the containers names because it's able to read the docker socket.
|
||||
* All 3 nodes run keepalived, at varying priorities. Since traefik is running as a swarm service and listening on TCP 80/443, requests made to the keepalived VIP and arriving at **any** of the swarm nodes will be forwarded to the traefik container (*no matter which node it's on*), and then onto the target backend.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Node failure
|
||||
|
||||
@@ -71,7 +71,7 @@ In the case of a failure (or scheduled maintenance) of one of the nodes, the fol
|
||||
* The **traefik** service is either restarted or unaffected, and as the backend containers stop/start and change IP, traefik is aware and updates accordingly.
|
||||
* The keepalived VIP continues to function on the remaining nodes, and docker swarm continues to forward any traffic received on TCP 80/443 to the appropriate node.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Node restore
|
||||
|
||||
@@ -82,7 +82,7 @@ When the failed (*or upgraded*) host is restored to service, the following is il
|
||||
* Existing containers which were migrated off the node are not migrated backend
|
||||
* Keepalived VIP regains full redundancy
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Total cluster failure
|
||||
|
||||
|
||||
@@ -59,7 +59,7 @@ Assuming a 3-node configuration, under normal circumstances the following is ill
|
||||
* The **traefik** service (*in swarm mode*) receives incoming requests (*on HTTP and HTTPS*), and forwards them to individual containers. Traefik knows the containers names because it's able to read the docker socket.
|
||||
* All 3 nodes run keepalived, at varying priorities. Since traefik is running as a swarm service and listening on TCP 80/443, requests made to the keepalived VIP and arriving at **any** of the swarm nodes will be forwarded to the traefik container (*no matter which node it's on*), and then onto the target backend.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Node failure
|
||||
|
||||
@@ -71,7 +71,7 @@ In the case of a failure (or scheduled maintenance) of one of the nodes, the fol
|
||||
* The **traefik** service is either restarted or unaffected, and as the backend containers stop/start and change IP, traefik is aware and updates accordingly.
|
||||
* The keepalived VIP continues to function on the remaining nodes, and docker swarm continues to forward any traffic received on TCP 80/443 to the appropriate node.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Node restore
|
||||
|
||||
@@ -82,7 +82,7 @@ When the failed (*or upgraded*) host is restored to service, the following is il
|
||||
* Existing containers which were migrated off the node are not migrated backend
|
||||
* Keepalived VIP regains full redundancy
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Total cluster failure
|
||||
|
||||
|
||||
@@ -13,7 +13,7 @@ Normally this is done using a HA loadbalancer, but since Docker Swarm aready pro
|
||||
|
||||
This is accomplished with the use of keepalived on at least two nodes.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Ingredients
|
||||
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
While Docker Swarm is great for keeping containers running (_and restarting those that fail_), it does nothing for persistent storage. This means if you actually want your containers to keep any data persistent across restarts (_hint: you do!_), you need to provide shared storage to every docker node.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Ingredients
|
||||
|
||||
|
||||
@@ -23,7 +23,7 @@ This is the role of Traefik Forward Auth.
|
||||
When employing Traefik Forward Auth as "[middleware](https://doc.traefik.io/traefik/middlewares/forwardauth/)", the forward-auth process sits in the middle of this transaction - traefik receives the incoming request, "checks in" with the auth server to determine whether or not further authentication is required. If the user is authenticated, the auth server returns a 200 response code, and Traefik is authorized to forward the request to the backend. If not, traefik passes the auth server response back to the user - this process will usually direct the user to an authentication provider (*[Google][tfa-google], [Keycloak][tfa-keycloak], and [Dex][tfa-dex-static] are common examples*), so that they can perform a login.
|
||||
|
||||
Illustrated below:
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
The advantage under this design is additional security. If I'm deploying a web app which I expect only an authenticated user to require access to (*unlike something intended to be accessed publically, like [Linx][linx]*), I'll pass the request through Traefik Forward Auth. The overhead is negligible, and the additional layer of security is well-worth it.
|
||||
|
||||
|
||||
@@ -11,7 +11,7 @@ There are some gaps to this approach though:
|
||||
|
||||
To deal with these gaps, we need a front-end load-balancer, and in this design, that role is provided by [Traefik](https://traefik.io/).
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
!!! tip
|
||||
In 2021, this recipe was updated for Traefik v2. There's really no reason to be using Traefikv1 anymore ;)
|
||||
@@ -233,7 +233,7 @@ root@raphael:~#
|
||||
|
||||
You should now be able to access[^1] your traefik instance on `https://traefik.<your domain\>` (*if your LetsEncrypt certificate is working*), or `http://<node IP\>:8080` (*if it's not*)- It'll look a little lonely currently (*below*), but we'll populate it as we add recipes :grin:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Summary
|
||||
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
Miniflux is a lightweight RSS reader, developed by [Frédéric Guillot](https://github.com/fguillot). (_Who also happens to be the developer of the favorite Open Source Kanban app, [Kanboard](/recipes/kanboard/)_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
I've [reviewed Miniflux in detail on my blog](https://www.funkypenguin.co.nz/review/miniflux-lightweight-self-hosted-rss-reader/), but features (among many) that I appreciate:
|
||||
|
||||
|
||||
@@ -18,27 +18,27 @@ IMO, the easiest Kubernetes cloud provider to experiment with is [DigitalOcean](
|
||||
|
||||
Create a project, and then from your project page, click **Manage** -> **Kubernetes (LTD)** in the left-hand panel:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Until DigitalOcean considers their Kubernetes offering to be "production ready", you'll need the additional step of clicking on **Enable Limited Access**:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
The _Enable Limited Access_ button changes to read _Create a Kubernetes Cluster_ . Cleeeek it:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
When prompted, choose some defaults for your first node pool (_your pool of "compute" resources for your cluster_), and give it a name. In more complex deployments, you can use this concept of "node pools" to run certain applications (_like an inconsequential nightly batch job_) on a particular class of compute instance (_such as cheap, preemptible instances_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
That's it! Have a sip of your 🍷, a bite of your :cheese:, and wait for your cluster to build. While you wait, follow the instructions to setup kubectl (if you don't already have it)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
DigitalOcean will provide you with a "kubeconfig" file to use to access your cluster. It's at the bottom of the page (_illustrated below_), and easy to miss (_in my experience_).
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Release the kubectl!
|
||||
|
||||
|
||||
@@ -69,7 +69,7 @@ We use a phone-home container, which calls a simple webhook on our haproxy VM, a
|
||||
|
||||
Here's a high-level diagram:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Overview
|
||||
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
[Helm](https://github.com/helm/helm) is a tool for managing Kubernetes "charts" (_think of it as an uber-polished collection of recipes_). Using one simple command, and by tweaking one simple config file (values.yaml), you can launch a complex stack. There are many publicly available helm charts for popular packages like [elasticsearch](https://github.com/helm/charts/tree/master/stable/elasticsearch), [ghost](https://github.com/helm/charts/tree/master/stable/ghost), [grafana](https://github.com/helm/charts/tree/master/stable/grafana), [mediawiki](https://github.com/helm/charts/tree/master/stable/mediawiki), etc.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Ingredients
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Unlike competing ingresses (*cough* nginx *cough*), the beautiful T
|
||||
|
||||
One of the advantages [Traefik](/kubernetes/ingress/traefik/) offers over [Nginx](/kubernetes/ingress/nginx/), is a native dashboard available in the open-source version (*Nginx+, the commercially-supported version, also includes a dashboard*).
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
!!! summary "Ingredients"
|
||||
|
||||
|
||||
@@ -12,7 +12,7 @@ Traefik natively includes some features which Nginx lacks:
|
||||
* [x] An elegant "middleware" implementation allowing certain requests to pass through additional layers of authentication
|
||||
* [x] A beautiful dashboard
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
!!! summary "Ingredients"
|
||||
|
||||
|
||||
@@ -22,23 +22,23 @@ Install the FRR package in pfsense, under **System -> Package Manager -> Availab
|
||||
|
||||
Under **Services -> FRR Global/Zebra**, enable FRR, set your router ID (*this will be your router's peer IP in MetalLB config*), and set a master password (*because apparently you have to, even though we don't use it*):
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Configure FRR BGP
|
||||
|
||||
Under **Services -> FRR BGP**, globally enable BGP, and set your local AS and router ID:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Configure FRR BGP Advanced
|
||||
|
||||
Use the tabs at the top of the FRR configuration to navigate to "**Advanced**"...
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
... and scroll down to **eBGP**. Check the checkbox titled "**Disable eBGP Require Policy**:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
!!! question "Isn't disabling a policy check a Bad Idea(tm)?"
|
||||
If you're an ISP, sure. If you're only using eBGP to share routes between MetalLB and pfsense, then applying policy is an unnecessary complication.[^1]
|
||||
@@ -58,13 +58,13 @@ It's useful to bundle our configurations within a "peer group" (*a collection of
|
||||
|
||||
Now add each node running MetalLB, as a BGP neighbor. Pick the peer-group you created above, and configure each neighbor's ASN:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Serving
|
||||
|
||||
Once you've added your neighbors, you should be able to use the FRR tab navigation (*it's weird, I know!*) to get to Status / BGP, and identify your neighbors, and all the routes learned from them. In the screenshot below, you'll note that **most** routes are learned from all the neighbors - that'll be service backed by a daemonset, running on all nodes. The `192.168.32.3/32` route, however, is only received from `192.168.33.22`, meaning only one node is running the pods backing this service, so only those pods are advertising the route to pfSense:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Troubleshooting
|
||||
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
Miniflux is a lightweight RSS reader, developed by [Frédéric Guillot](https://github.com/fguillot). (_Who also happens to be the developer of the favorite Open Source Kanban app, [Kanboard](/recipes/kanboard/)_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
I've [reviewed Miniflux in detail on my blog](https://www.funkypenguin.co.nz/review/miniflux-lightweight-self-hosted-rss-reader/), but features (among many) that I appreciate:
|
||||
|
||||
|
||||
@@ -14,7 +14,7 @@ They're still not very secret though, and you certainly wouldn't want to be stor
|
||||
|
||||
An elegant solution to this problem is Bitnami Labs' Sealed Secrets.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
A "[SealedSecret](https://github.com/bitnami-labs/sealed-secrets)" can only be decrypted (*and turned back into a regular Secret*) by the controller in the target cluster. (*or by a controller in another cluster which has been primed with your own private/public pair)* This means the SealedSecret is safe to store and expose anywhere.
|
||||
|
||||
|
||||
@@ -113,7 +113,7 @@ storage: 1Gi
|
||||
|
||||
And here's what my snapshot list looks like after a few days:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Snapshot a non-Kubernetes volume (optional)
|
||||
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
"Premix" is a private repository shared with [GitHub sponsors](https://github.com/sponsors/funkypenguin), which contains the necessary files and automation to quickly deploy any recipe, or even an entire [swarm](/docker/) / [cluster](/kubernetes/)! :muscle:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Benefits
|
||||
|
||||
|
||||
@@ -5,7 +5,7 @@ description: A self-hosted internet archiving solution
|
||||
|
||||
[ArchiveBox](https://github.com/ArchiveBox/ArchiveBox) is a self-hosted internet archiving solution to collect and save sites you wish to view offline.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
@@ -5,7 +5,7 @@
|
||||
|
||||
[Headphones](https://github.com/rembo10/headphones) is an automated music downloader for NZB and Torrent, written in Python. It supports [SABnzbd][sabnzbd], [NZBget][nzbget], Transmission, µTorrent, Deluge and Blackhole.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -8,7 +8,7 @@ Once the cutting edge of the "internet" (_pre-world-wide-web and mosiac days_),
|
||||
|
||||
A good starter for the usenet scene is <https://www.reddit.com/r/usenet/>. Because it's so damn complicated, a host of automated tools exist to automate the process of finding, downloading, and managing content. The tools included in this recipe are as per the following example:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
This recipe presents a method to combine these tools into a single swarm deployment, and make them available securely.
|
||||
|
||||
@@ -55,7 +55,7 @@ Since this recipe is so long, and so many of the tools are optional to the final
|
||||
|
||||
Related:
|
||||
|
||||
* [X] [Traefik Forward Auth](docker-swarm/traefik-forward-auth/) to secure your Traefik-exposed services with an additional layer of authentication
|
||||
* [X] [Traefik Forward Auth](/docker-swarm/traefik-forward-auth/) to secure your Traefik-exposed services with an additional layer of authentication
|
||||
|
||||
## Preparation
|
||||
|
||||
|
||||
@@ -11,7 +11,7 @@ description: Jackett works as a proxy server, standardizing your apps' (Radarr /
|
||||
|
||||
This allows for getting recent uploads (like RSS) and performing searches. Jackett is a single repository of maintained indexer scraping & translation logic - removing the burden from other apps.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -16,7 +16,7 @@ description: LazyLibrarian is a tool to follow authors and manage your ebook / a
|
||||
* AutoAdd feature for book management tools like Calibre which must have books in flattened directory structure, or use calibre to import your books into an existing calibre library
|
||||
* LazyLibrarian can also be used to search for and download magazines, and monitor for new issues
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -9,7 +9,7 @@ description: Lidarr is an automated music downloader for NZB and Torrent
|
||||
|
||||
[Lidarr](https://lidarr.audio/) is an automated music downloader for NZB and Torrent. It performs the same function as [Headphones](/recipes/autopirate/headphones), but is written using the same(ish) codebase as [Radarr][radarr] and [Sonarr][sonarr]. It's blazingly fast, and includes beautiful album/artist art. Lidarr supports [SABnzbd][sabnzbd], [NZBGet][nzbget], Transmission, µTorrent, Deluge and Blackhole (_just like Sonarr / Radarr_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -10,7 +10,7 @@ description: NZBHydra is a meta search engine for NZB indexers, and can be used
|
||||
|
||||
[NZBHydra2](https://github.com/theotherp/nzbhydra2) is a meta search for NZB indexers. It provides easy access to a number of raw and newznab based indexers. You can search all your indexers from one place and use it as an indexer source for tools like Sonarr, Radarr or CouchPotato.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
@@ -18,7 +18,7 @@ User management system (_supports plex.tv, Emby and local accounts_)
|
||||
* Will show if the request is already on plex or even if it's already monitored.
|
||||
* Automatically updates the status of requests when they are available on Plex/Emby/Jellyfin
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -12,7 +12,7 @@ description: Prowlarr aggregates nzb/torrent searches. Imagine NZBHydra and Jack
|
||||
|
||||
Prowlarr supports management of both Torrent Trackers and Usenet Indexers. It integrates seamlessly with [Lidarr][lidarr], [Mylar3][mylar], [Radarr][radarr], [Readarr][readarr], and [Sonarr][sonarr] offering complete management of your indexers with no per app Indexer setup required!
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Fancy features include:
|
||||
|
||||
|
||||
@@ -24,7 +24,7 @@ description: Radarr is a tool for finding, downloading and managing movies, and
|
||||
* And a beautiful UI
|
||||
* Importing Metadata such as trailers or subtitles
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -10,7 +10,7 @@ description: Readarr is "Sonarr/Radarr for eBooks and audiobooks, and plays perf
|
||||
|
||||
[Readarr](https://github.com/Readarr/Readarr), in the fine tradition of [Radarr][radarr] and [Sonarr][sonarr], is a tool for "sourcing" eBooks, using usenet or bittorrent indexers.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
@@ -10,7 +10,7 @@ description: ruTorrent (looks like uTorrent) is a popular web UI frontend to rto
|
||||
|
||||
[RTorrent](http://rakshasa.github.io/rtorrent) is a popular CLI-based bittorrent client, and [ruTorrent](https://github.com/Novik/ruTorrent) is a powerful web interface for rtorrent.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Choose incoming port
|
||||
|
||||
|
||||
@@ -12,7 +12,7 @@ description: SABnzbd is a tool for downloading "content" from Usenet providers,
|
||||
|
||||
SABnzbd is a workhorse of the stack. It takes .nzb files as input (_manually or from other [autopirate](/recipes/autopirate/) stack tools_), then connects to your chosen Usenet provider, downloads all the individual binaries referenced by the .nzb, and then tests/repairs/combines/uncompresses them all into the final result - media files.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -10,7 +10,7 @@ description: Sonarr is a tool for finding, downloading and managing TV series*,
|
||||
|
||||
[Sonarr](https://sonarr.tv/) is a tool for finding, downloading and managing your TV series.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Inclusion into AutoPirate
|
||||
|
||||
|
||||
@@ -13,7 +13,7 @@ Heard about the [latest password breach](https://www.databreaches.net) (*since l
|
||||
|
||||
Enter Bitwarden..
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Bitwarden is a free and open source password management solution for individuals, teams, and business organizations. While Bitwarden does offer a paid / hosted version, the free version comes with the following (*better than any other free password manager!*):
|
||||
|
||||
|
||||
@@ -9,7 +9,7 @@ BookStack is a simple, self-hosted, easy-to-use platform for organising and stor
|
||||
|
||||
A friendly middle ground between heavyweights like MediaWiki or Confluence and [Gollum](/recipes/gollum/), BookStack relies on a database backend (so searching and versioning is easy), but limits itself to a pre-defined, 3-tier structure (book, chapter, page). The result is a lightweight, approachable personal documentation stack, which includes search and Markdown editing.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
I like to protect my public-facing web UIs with an [oauth_proxy](/reference/oauth_proxy), ensuring that if an application bug (or a user misconfiguration) exposes the app to unplanned public scrutiny, I have a second layer of defense.
|
||||
|
||||
|
||||
@@ -9,7 +9,7 @@ The [AutoPirate](/recipes/autopirate/) recipe includes [Lazy Librarian](https://
|
||||
|
||||
[Calibre-Web](https://github.com/janeczku/calibre-web) could be described as "_[Plex](/recipes/plex/) (or [Emby](/recipes/emby/)) for eBooks_" - it's a web-based interface to manage your eBook library, screenshot below:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Of course, you probably already manage your eBooks using the excellent [Calibre](https://calibre-ebook.com/), but this is primarily a (_powerful_) desktop application. Calibre-Web is an alternative way to manage / view your existing Calibre database, meaning you can continue to use Calibre on your desktop if you wish.
|
||||
|
||||
|
||||
@@ -8,7 +8,7 @@ Collabora Online Development Edition (or "[CODE](https://www.collaboraoffice.com
|
||||
|
||||
It's basically the [LibreOffice](https://www.libreoffice.org/) interface in a web-browser. CODE is not a standalone app, it's a backend intended to be accessed via "WOPI" from an existing interface (_in our case, [NextCloud](/recipes/nextcloud/)_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Ingredients
|
||||
|
||||
@@ -36,7 +36,7 @@ What if we're running multiple nodes in our swarm, and nginx ends up on a differ
|
||||
|
||||
Here's a (_highly technical_) diagram to illustrate:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Setup data locations
|
||||
|
||||
@@ -301,7 +301,7 @@ Visit `https://collabora.<yourdomain\>/l/loleaflet/dist/admin/admin.html` and co
|
||||
|
||||
In NextCloud, Install the **Collabora Online** app (<https://apps.nextcloud.com/apps/richdocuments>), and then under **Settings -> Collabora Online**, set your Collabora Online Server to ```https://collabora.<your domain>```
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Now browse your NextCloud files. Click the plus (+) sign to create a new document, and create either a new document, spreadsheet, or presentation. Name your document and then click on it. If Collabora is setup correctly, you'll shortly enter into the rich editing interface provided by Collabora :)
|
||||
|
||||
|
||||
@@ -9,7 +9,7 @@ Are you a [l33t h@x0r](https://en.wikipedia.org/wiki/Hackers_(film))? Do you nee
|
||||
|
||||
[^1]: [Government Communications Headquarters](https://en.wikipedia.org/wiki/GCHQ), commonly known as GCHQ, is an intelligence and security organisation responsible for providing signals intelligence and information assurance to the government and armed forces of the United Kingdom
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[CyberChef](https://github.com/gchq/CyberChef) is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: A boring recipe to backup your exciting stuff. Boring is good.
|
||||
|
||||
Intro
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[Duplicity](https://duplicity.gitlab.io/duplicity-web/) backs directories by producing encrypted tar-format volumes and uploading them to a remote or local file server. Because duplicity uses librsync, the incremental archives are space efficient and only record the parts of files that have changed since the last backup. Because duplicity uses GnuPG to encrypt and/or sign these archives, they will be safe from spying and/or modification by the server.
|
||||
|
||||
|
||||
@@ -11,7 +11,7 @@ Don't be like [Cameron](http://haltandcatchfire.wikia.com/wiki/Cameron_Howe). Ba
|
||||
|
||||
ElkarBackup is a free open-source backup solution based on RSync/RSnapshot. It's basically a web wrapper around rsync/rsnapshot, which means that your backups are just files on a filesystem, utilising hardlinks for tracking incremental changes. I find this result more reassuring than a blob of compressed, (encrypted?) data that [more sophisticated backup solutions](/recipes/duplicity/) would produce for you.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Details
|
||||
|
||||
@@ -153,11 +153,11 @@ Launch the ElkarBackup stack by running ```docker stack deploy elkarbackup -c <p
|
||||
|
||||
Log into your new instance at https://**YOUR-FQDN**, with user "root" and the password default password "root":
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
First thing you do, change your password, using the gear icon, and "Change Password" link:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Have a read of the [Elkarbackup Docs](https://docs.elkarbackup.org/docs/introduction.html) - they introduce the concept of **clients** (_hosts containing data to be backed up_), **jobs** (_what data gets backed up_), **policies** (_when is data backed up and how long is it kept_).
|
||||
|
||||
@@ -216,7 +216,7 @@ Repeat after me : "**It's not a backup unless you've tested a restore**"
|
||||
|
||||
To restore files form a job, click on the "Restore" button in the WebUI, while on the **Jobs** tab:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
This takes you to a list of backup names and file paths. You can choose to download the entire contents of the backup from your browser as a .tar.gz, or to restore the backup to the client. If you click on the **name** of the backup, you can also drill down into the file structure, choosing to restore a single file or directory.
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ description: Kick-ass media player!
|
||||
|
||||
[Emby](https://emby.media/) (_think "M.B." or "Media Browser"_) is best described as "_like [Plex](/recipes/plex/) but different_" 😁 - It's a bit geekier and less polished than Plex, but it allows for more flexibility and customization.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
I've started experimenting with Emby as an alternative to Plex, because of the advanced [parental controls](https://github.com/MediaBrowser/Wiki/wiki/Parental-Controls) it offers. Based on my experimentation thus far, I have a "**kid-safe**" profile which automatically logs in, and only displays kid-safe content, based on ratings.
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Ghost - Beautiful online publicatio (who you gonna call?)
|
||||
|
||||
[Ghost](https://ghost.org) is "a fully open source, hackable platform for building and running a modern online publication."
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -16,7 +16,7 @@ Gollum pages:
|
||||
* Can be edited with your favourite system editor or IDE (_changes will be visible after committing_) or with the built-in web interface.
|
||||
* Can be displayed in all versions (_commits_).
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
As you'll note in the (_real world_) screenshot above, my requirements for a personal wiki are:
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Assist your home automation
|
||||
|
||||
Home Assistant is a home automation platform written in Python, with extensive support for 3rd-party home-automation platforms including Xaomi, Phillips Hue, and a [bazillion](https://home-assistant.io/components/) others.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
This recipie combines the [extensibility](https://home-assistant.io/components/) of [Home Assistant](https://home-assistant.io/) with the flexibility of [InfluxDB](https://docs.influxdata.com/influxdb/v1.4/) (_for time series data store_) and [Grafana](https://grafana.com/) (_for **beautiful** visualisation of that data_).
|
||||
|
||||
|
||||
@@ -8,7 +8,7 @@ description: Automate your fake Instagram life with automated fakery!
|
||||
|
||||
What's an Instagram bot? Basically, you feed the bot your Instagram user/password, and it executes follows/unfollows/likes/comments on your behalf based on rules you set. (_I set my bot to like one photo tagged with "[#penguin](https://www.instagram.com/explore/tags/penguin/?hl=en)" per-run_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Great power, right? A client (_yes, you can [hire](https://www.funkypenguin.co.nz/) me!_) asked me to integrate InstaPy into their swarm, and this recipe is the result.
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@
|
||||
|
||||
The intention of this recipe is to provide a local IPFS cluster for the purpose of providing persistent storage for the various components of the recipes
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Description. IPFS is a peer-to-peer distributed file system that seeks to connect all computing devices with the same system of files. In some ways, IPFS is similar to the World Wide Web, but IPFS could be seen as a single BitTorrent swarm, exchanging objects within one Git repository.
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ description: Jellyfin is best described as "like Emby but really FOSS"
|
||||
|
||||
[Jellyfin](https://jellyfin.org/) is best described as "_like [Emby](/recipes/emby) but really [FOSS](https://en.wikipedia.org/wiki/Free_and_open-source_software)_".
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
If it looks very similar as Emby, is because it started as a fork of it, but it has evolved since them. For a complete explanation of the why, look [here](https://jellyfin.org/docs/general/about.html).
|
||||
|
||||
|
||||
@@ -19,7 +19,7 @@ Features include:
|
||||
* Free, open source and self-hosted
|
||||
* Super simple installation
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -24,11 +24,11 @@ You start in the "Master" realm - but mouseover the realm name, to a dropdown bo
|
||||
|
||||
### Create Realm
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Enter a name for your new realm, and click "_Create_":
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Setup User Federation
|
||||
|
||||
@@ -44,7 +44,7 @@ Once in the desired realm, click on **User Federation**, and click **Add Provide
|
||||
|
||||
Save your changes, and then navigate back to "User Federation" > Your LDAP name > Mappers:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
For each of the following mappers, click the name, and set the "_Read Only_" flag to "_Off_" (_this enables 2-way sync between KeyCloak and OpenLDAP_)
|
||||
|
||||
@@ -53,7 +53,7 @@ For each of the following mappers, click the name, and set the "_Read Only_" fla
|
||||
* email
|
||||
* first name
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Summary
|
||||
|
||||
|
||||
@@ -16,17 +16,17 @@ Existing:
|
||||
|
||||
Within the "Master" realm (_no need for more realms yet_), navigate to **Manage** -> **Users**, and then click **Add User** at the top right:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Populate your new user's username (it's the only mandatory field)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Set User Credentials
|
||||
|
||||
Once your user is created, to set their password, click on the "**Credentials**" tab, and procede to reset it. Set the password to non-temporary, unless you like extra work!
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Summary
|
||||
|
||||
|
||||
@@ -8,7 +8,7 @@ description: Kick-ass OIDC and identity management
|
||||
|
||||
KeyCloak's OpenID provider can also be used in combination with [Traefik Forward Auth](/docker-swarm/traefik-forward-auth/), to protect [vulnerable services](/recipes/autopirate/nzbget/) with an extra layer of authentication.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -22,11 +22,11 @@ Having an authentication provider is not much use until you start authenticating
|
||||
|
||||
Within the "Master" realm (*no need for more realms yet*), navigate to **Clients**, and then click **Create** at the top right:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Enter a name for your client (*remember, we're authenticating **applications** now, not users, so use an application-specific name*):
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Configure Client
|
||||
|
||||
@@ -35,13 +35,13 @@ Once your client is created, set at **least** the following, and click **Save**
|
||||
* **Access Type** : Confidential
|
||||
* **Valid Redirect URIs** : <The URIs you want to protect\>
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
### Retrieve Client Secret
|
||||
|
||||
Now that you've changed the access type, and clicked **Save**, an additional **Credentials** tab appears at the top of the window. Click on the tab, and capture the KeyCloak-generated secret. This secret, plus your client name, is required to authenticate against KeyCloak via OIDC.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Summary
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Bazinga! Comic book management FTW!
|
||||
|
||||
So you've just watched a bunch of superhero movies, and you're suddenly inspired to deep-dive into the weird world of comic books? You're already rocking [AutoPirate](/recipes/autopirate/) with [Mylar](/recipes/autopirate/mylar/) and [NZBGet](/recipes/autopirate/nzbget/) to grab content, but how to manage and enjoy your growing collection?
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[Komga](https://komga.org/) is a media server with a beautifully slick interface, allowing you to read your comics / manga in CBZ, CBR, PDF and epub format. Komga includes an integrated web reader, as well as a [Tachiyomi](https://tachiyomi.org/) plugin and an OPDS server for integration with other mobile apps such as [Chunky on iPad](http://chunkyreader.com/).
|
||||
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
|
||||
Miniflux is a lightweight RSS reader, developed by [Frédéric Guillot](https://github.com/fguillot). (_Who also happens to be the developer of the favorite Open Source Kanban app, [Kanboard](/recipes/kanboard/)_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
I've [reviewed Miniflux in detail on my blog](https://www.funkypenguin.co.nz/review/miniflux-lightweight-self-hosted-rss-reader/), but features (among many) that I appreciate:
|
||||
|
||||
|
||||
@@ -9,7 +9,7 @@ description: A tasty tool to manage your meals and shopping list, on Docker swar
|
||||
|
||||
Easily add recipes into your database by providing the url[^penguinfood], and mealie will automatically import the relevant data or add a family recipe with the UI editor.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Mealie also provides a secure API for interactions from 3rd party applications.
|
||||
|
||||
@@ -88,7 +88,7 @@ networks:
|
||||
|
||||
Launch the mealie stack by running ```docker stack deploy mealie -c <path -to-docker-compose.yml>```. The first time you access Mealie at https://**YOUR FQDN**, you might think there's something wrong. There are **no** recipes, and no instructions. Hover over the little plus sign at the bottom right, and within a second, two icons appear. Click the "link" icon to import a recipe from a URL:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[^penguinfood]: I scraped all these recipes from <https://www.food.com/search/penguin>
|
||||
[^1]: If you plan to use Mealie for fancy things like an early-morning alarm to defrost the chicken, you may need to customize the [Traefik Forward Auth][tfa] rules, or even remove them entirely, for unauthenticated API access.
|
||||
|
||||
@@ -6,7 +6,7 @@ description: A lightweight minimalist RSS reader
|
||||
|
||||
Miniflux is a lightweight RSS reader, developed by [Frédéric Guillot](https://github.com/fguillot). (_Who also happens to be the developer of the favorite Open Source Kanban app, [Kanboard](/recipes/kanboard/)_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
I've [reviewed Miniflux in detail on my blog](https://www.funkypenguin.co.nz/review/miniflux-lightweight-self-hosted-rss-reader/), but features (among many) that I appreciate:
|
||||
|
||||
|
||||
@@ -11,7 +11,7 @@ However, at its simplest, Minio allows you to expose a local filestructure via t
|
||||
|
||||
Under a more advanced configuration, Minio runs in distributed mode, with [features](https://docs.min.io/minio/baremetal/concepts/feature-overview.html) including high-availability, mirroring, erasure-coding, and "bitrot detection".
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Possible use-cases:
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ description: Network resource monitoring tool for quick analysis
|
||||
|
||||
Munin is a networked resource monitoring tool that can help analyze resource trends and "what just happened to kill our performance?" problems. It is designed to be very plug and play. A default installation provides a lot of graphs with almost no work.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Using Munin you can easily monitor the performance of your computers, networks, SANs, applications, weather measurements and whatever comes to mind. It makes it easy to determine "what's different today" when a performance problem crops up. It makes it easy to see how you're doing capacity-wise on any resources.
|
||||
|
||||
|
||||
@@ -8,7 +8,7 @@ description: Share docs. Backup files. Share stuff.
|
||||
|
||||
- <https://en.wikipedia.org/wiki/Nextcloud>
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
This recipe is based on the official NextCloud docker image, but includes seprate containers ofor the database (_MariaDB_), Redis (_for transactional locking_), Apache Solr (_for full-text searching_), automated database backup, (_you *do* backup the stuff you care about, right?_) and a separate cron container for running NextCloud's 15-min crons.
|
||||
|
||||
|
||||
@@ -12,7 +12,7 @@ Nightscout is "*...an open source, DIY project that allows real time access to a
|
||||
|
||||
NightScout frees you from the CGM's supplier's limited and proprietary app, and unlocks advanced charting, alarming, and sharing features :muscle:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[Nightscout](https://nightscout.github.io/) is _the_ standard for open-source CGM data collection, used by diabetics and those who love them, to store, share, and retrieve blood-glocuse data, in order to live healthier and happier lives. It's used as the data sharing/syncing backend for all the popular smartphone apps, including [xDrip+](https://github.com/NightscoutFoundation/xDrip) (*Android*) and [Spike App](https://spike-app.com/) (*iOS*).
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Spy on yourself.
|
||||
|
||||
[OwnTracks](https://owntracks.org/) allows you to keep track of your own location. You can build your private location diary or share it with your family and friends. OwnTracks is open-source and uses open protocols for communication so you can be sure your data stays secure and private.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Using a smartphone app, OwnTracks allows you to collect and analyse your own location data **without** sharing this data with a cloud provider (_i.e. Apple, Google_). Potential use cases are:
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Easily index, search, and view archive all of your scanned dead-tre
|
||||
|
||||
Paper is a nightmare. Environmental issues aside, there’s no excuse for it in the 21st century. It takes up space, collects dust, doesn’t support any form of a search feature, indexing is tedious, it’s heavy and prone to damage & loss. [^1] Paperless NG will OCR, index, and store data about your documents so they are easy to search and view, unlike that hulking metal file cabinet you have in your office.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ description: ML-powered private photo hosting
|
||||
|
||||
[Photoprism™](https://github.com/photoprism/photoprism) "is a server-based application for browsing, organizing and sharing your personal photo collection. It makes use of the latest technologies to automatically tag and find pictures without getting in your way. Say goodbye to solutions that force you to upload your visual memories to the cloud."
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Is that IP address in use?
|
||||
|
||||
phpIPAM is an open-source web IP address management application (_IPAM_). Its goal is to provide light, modern and useful IP address management. It is php-based application with MySQL database backend, using jQuery libraries, ajax and HTML5/CSS3 features.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
phpIPAM fulfils a non-sexy, but important role - It helps you manage your IP address allocation.
|
||||
|
||||
|
||||
@@ -11,7 +11,7 @@ description: A UI to make Docker less geeky
|
||||
|
||||
Portainer attempts to take the "geekiness" out of containers, by wrapping all the jargon and complexity in a shiny UI and some simple abstractions. It's a great addition to any stack, especially if you're just starting your containerization journey!
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
@@ -111,7 +111,7 @@ Launch the Portainer stack by running ```docker stack deploy portainer -c <path
|
||||
|
||||
Log into your new instance at https://**YOUR-FQDN**. You'll be prompted to set your admin user/password on first login. Start at "Home", and click on "Primary" to manage your swarm (*you can manage multiple swarms via one Portainer instance using the agent*):
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[^1]: There are [some schenanigans](https://www.reddit.com/r/docker/comments/au9wnu/linuxserverio_templates_for_portainer/) you can do to install LinuxServer.io templates in Portainer. Don't go crying to them for support though! :crying_cat_face:
|
||||
|
||||
|
||||
@@ -7,7 +7,7 @@ description: A private imgur/pastebin, running on Docker
|
||||
|
||||
PrivateBin is a minimalist, open source online pastebin where the server (can) has zero knowledge of pasted data. We all need to paste data / log files somewhere when it doesn't make sense to paste it inline. With PrivateBin, you can own the hosting, access, and eventual deletion of this data.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: A git-based wiki with auth and registration
|
||||
|
||||
Realms is a git-based wiki (_like [Gollum](/recipes/gollum/), but with basic authentication and registration_)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Stalk your ex on Facebook in your feedreader!
|
||||
|
||||
Do you hate having to access multiple sites to view specific content? [RSS-Bridge](https://github.com/RSS-Bridge/rss-bridge) can convert content from a wide variety of websites (*such as Reddit, Facebook, Twitter*) so that it can be viewed in a structured and consistent way, all from one place (Your feed reader)
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Data is beautiful
|
||||
|
||||
[Swarmprom](https://github.com/stefanprodan/swarmprom) is a starter kit for Docker Swarm monitoring with [Prometheus](https://prometheus.io/), [Grafana](http://grafana.org/), [cAdvisor](https://github.com/google/cadvisor), [Node Exporter](https://github.com/prometheus/node_exporter), [Alert Manager](https://github.com/prometheus/alertmanager) and [Unsee](https://github.com/cloudflare/unsee). And it's **damn** sexy. See for yourself:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
So what do all these components do?
|
||||
|
||||
|
||||
@@ -4,7 +4,7 @@ description: Neat one-sentence description of recipe for social media previews
|
||||
|
||||
# <///RECIPE NAME>
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[Linx](https://github.com/andreimarcu/linx-server) is self-hosted file/media-sharing service, which features:
|
||||
|
||||
|
||||
@@ -10,7 +10,7 @@ description: Geeky RSS reader
|
||||
* Filtering (discard all articles with title matching "trump")
|
||||
* Sharing articles via a unique public URL/feed
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
--8<-- "recipe-standard-ingredients.md"
|
||||
|
||||
|
||||
@@ -8,7 +8,7 @@ Wallabag is a self-hosted webapp which allows you to save URLs to "read later",
|
||||
|
||||
All saved data (_pages, annotations, images, tags, etc_) are stored on your own server, and can be shared/exported in a variety of formats, including ePub and PDF.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
There are plugins for [Chrome](https://chrome.google.com/webstore/detail/wallabagger/gbmgphmejlcoihgedabhgjdkcahacjlj) and [Firefox](https://addons.mozilla.org/firefox/addon/wallabagger/), as well as apps for [iOS](https://appsto.re/fr/YeqYfb.i), [Android](https://play.google.com/store/apps/details?id=fr.gaulupeau.apps.InThePoche), etc. Wallabag will also integrate nicely with my favorite RSS reader, [Miniflux](https://miniflux.net/) (_for which there is an [existing recipe](/recipes/miniflux)_).
|
||||
|
||||
@@ -174,7 +174,7 @@ You'll have noticed redis, plus the pocket/instapaper-importing containers inclu
|
||||
|
||||
Even with all these elements in place, you still need to enable Redis under Internal Settings -> Import, via the **admin** user in the webUI. Here's a screenshot to help you find it:
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
[^1]: If you wanted to expose the Wekan UI directly, you could remove the traefik-forward-auth from the design. I found the iOS app to be unreliable and clunky, so elected to leave my traefik-forward-auth enabled, and to simply use the webUI on my mobile devices instead. YMMMV.
|
||||
|
||||
|
||||
@@ -6,7 +6,7 @@ description: Terminal in a browser, baby!
|
||||
|
||||
[Wetty](https://github.com/krishnasrinivas/wetty) is a responsive, modern terminal, in your web browser. Yes, your browser. When combined with secure authentication and SSL encryption, it becomes a useful tool for quick and easy remote access.
|
||||
|
||||

|
||||
{ loading=lazy }
|
||||
|
||||
## Why would you need SSH in a browser window?
|
||||
|
||||
|
||||
@@ -4,38 +4,36 @@ In order to avoid IP addressing conflicts as we bring swarm networks up/down, we
|
||||
|
||||
| Network | Range |
|
||||
|-----------------------------------------------------------------------------------------------------------------------|----------------|
|
||||
| [Traefik](https://geek-cookbook.funkypenguin.co.nz/docker-swarm/traefik/) | _unspecified_ |
|
||||
| [Docker-cleanup](https://geek-cookbook.funkypenguin.co.nz/docker-swarm/docker-swarm-mode/#setup-automated-cleanup) | 172.16.0.0/24 |
|
||||
| [Mail Server](https://geek-cookbook.funkypenguin.co.nz/recipes/mail/) | 172.16.1.0/24 |
|
||||
| [Gitlab](https://geek-cookbook.funkypenguin.co.nz/recipes/gitlab/) | 172.16.2.0/24 |
|
||||
| [Wekan](https://geek-cookbook.funkypenguin.co.nz/recipes/wekan/) | 172.16.3.0/24 |
|
||||
| [NightScout](https://geek-cookbook.funkypenguin.co.nz/recipes/nightscout/) | 172.16.4.0/24 |
|
||||
| [Tiny Tiny RSS](https://geek-cookbook.funkypenguin.co.nz/recipes/tiny-tiny-rss/) | 172.16.5.0/24 |
|
||||
| [Huginn](https://geek-cookbook.funkypenguin.co.nz/recipes/huginn/) | 172.16.6.0/24 |
|
||||
| [Gollum](https://geek-cookbook.funkypenguin.co.nz/recipes/gollum/) | 172.16.7.0/24 |
|
||||
| [Polr](https://geek-cookbook.funkypenguin.co.nz/recipes/polr/) | 172.16.9.0/24 |
|
||||
| [Duplicity](https://geek-cookbook.funkypenguin.co.nz/recipes/duplicity/) | 172.16.10.0/24 |
|
||||
| [Autopirate](https://geek-cookbook.funkypenguin.co.nz/recipes/autopirate/) | 172.16.11.0/24 |
|
||||
| [Nextcloud](https://geek-cookbook.funkypenguin.co.nz/recipes/nextcloud/) | 172.16.12.0/24 |
|
||||
| [Portainer](https://geek-cookbook.funkypenguin.co.nz/recipes/portainer/) | 172.16.13.0/24 |
|
||||
| [Home Assistant](https://geek-cookbook.funkypenguin.co.nz/recipes/homeassistant/) | 172.16.14.0/24 |
|
||||
| [OwnTracks](https://geek-cookbook.funkypenguin.co.nz/recipes/owntracks/) | 172.16.15.0/24 |
|
||||
| [Plex](https://geek-cookbook.funkypenguin.co.nz/recipes/plex/) | 172.16.16.0/24 |
|
||||
| [Calibre-Web](https://geek-cookbook.funkypenguin.co.nz/recipes/calibre-web/) | 172.16.18.0/24 |
|
||||
| [Wallabag](https://geek-cookbook.funkypenguin.co.nz/recipes/wallabag/) | 172.16.19.0/24 |
|
||||
| [InstaPy](https://geek-cookbook.funkypenguin.co.nz/recipes/instapy/) | 172.16.20.0/24 |
|
||||
| [Archivy](https://geek-cookbook.funkypenguin.co.nz/recipes/archivy/) | 172.16.21.0/24 |
|
||||
| [MiniFlux](https://geek-cookbook.funkypenguin.co.nz/recipes/miniflux/) | 172.16.22.0/24 |
|
||||
| [Gitlab Runner](https://geek-cookbook.funkypenguin.co.nz/recipes/gitlab-runner/) | 172.16.23.0/24 |
|
||||
| [Bookstack](https://geek-cookbook.funkypenguin.co.nz/recipes/bookstack/) | 172.16.33.0/24 |
|
||||
| [Swarmprom](https://geek-cookbook.funkypenguin.co.nz/recipes/swarmprom/) | 172.16.34.0/24 |
|
||||
| [Realms](https://geek-cookbook.funkypenguin.co.nz/recipes/realms/) | 172.16.35.0/24 |
|
||||
| [ElkarBackup](https://geek-cookbook.funkypenguin.co.nz/recipes/elkarbackup/) | 172.16.36.0/24 |
|
||||
| [OpenLDAP](https://geek-cookbook.funkypenguin.co.nz/recipes/openldap/) | 172.16.39.0/24 |
|
||||
| [PrivateBin](https://geek-cookbook.funkypenguin.co.nz/recipes/privatebin/) | 172.16.41.0/24 |
|
||||
| [Wetty](https://geek-cookbook.funkypenguin.co.nz/recipes/wetty/) | 172.16.45.0/24 |
|
||||
| [phpIPAM](https://geek-cookbook.funkypenguin.co.nz/recipes/phpipam/) | 172.16.47.0/24 |
|
||||
| [KeyCloak](https://geek-cookbook.funkypenguin.co.nz/recipes/keycloak/) | 172.16.49.0/24 |
|
||||
| [Duplicati](https://geek-cookbook.funkypenguin.co.nz/recipes/duplicati/) | 172.16.55.0/24 |
|
||||
| [Restic](https://geek-cookbook.funkypenguin.co.nz/recipes/restic/) | 172.16.56.0/24 |
|
||||
| [Paperless NG](https://geek-cookbook.funkypenguin.co.nz/recipes/paperless/) | 172.16.58.0/24 |
|
||||
| [Traefik](/docker-swarm/traefik/) | _unspecified_ |
|
||||
| [Docker-cleanup](/docker-swarm/docker-swarm-mode/#setup-automated-cleanup) | 172.16.0.0/24 |
|
||||
| [Mail Server](/recipes/mail/) | 172.16.1.0/24 |
|
||||
| [Gitlab](/recipes/gitlab/) | 172.16.2.0/24 |
|
||||
| [Wekan](/recipes/wekan/) | 172.16.3.0/24 |
|
||||
| [NightScout](/recipes/nightscout/) | 172.16.4.0/24 |
|
||||
| [Tiny Tiny RSS](/recipes/tiny-tiny-rss/) | 172.16.5.0/24 |
|
||||
| [Huginn](/recipes/huginn/) | 172.16.6.0/24 |
|
||||
| [Gollum](/recipes/gollum/) | 172.16.7.0/24 |
|
||||
| [Duplicity](/recipes/duplicity/) | 172.16.10.0/24 |
|
||||
| [Autopirate](/recipes/autopirate/) | 172.16.11.0/24 |
|
||||
| [Nextcloud](/recipes/nextcloud/) | 172.16.12.0/24 |
|
||||
| [Portainer](/recipes/portainer/) | 172.16.13.0/24 |
|
||||
| [Home Assistant](/recipes/homeassistant/) | 172.16.14.0/24 |
|
||||
| [OwnTracks](/recipes/owntracks/) | 172.16.15.0/24 |
|
||||
| [Plex](/recipes/plex/) | 172.16.16.0/24 |
|
||||
| [Calibre-Web](/recipes/calibre-web/) | 172.16.18.0/24 |
|
||||
| [Wallabag](/recipes/wallabag/) | 172.16.19.0/24 |
|
||||
| [InstaPy](/recipes/instapy/) | 172.16.20.0/24 |
|
||||
| [MiniFlux](/recipes/miniflux/) | 172.16.22.0/24 |
|
||||
| [Gitlab Runner](/recipes/gitlab-runner/) | 172.16.23.0/24 |
|
||||
| [Bookstack](/recipes/bookstack/) | 172.16.33.0/24 |
|
||||
| [Swarmprom](/recipes/swarmprom/) | 172.16.34.0/24 |
|
||||
| [Realms](/recipes/realms/) | 172.16.35.0/24 |
|
||||
| [ElkarBackup](/recipes/elkarbackup/) | 172.16.36.0/24 |
|
||||
| [OpenLDAP](/recipes/openldap/) | 172.16.39.0/24 |
|
||||
| [PrivateBin](/recipes/privatebin/) | 172.16.41.0/24 |
|
||||
| [Wetty](/recipes/wetty/) | 172.16.45.0/24 |
|
||||
| [phpIPAM](/recipes/phpipam/) | 172.16.47.0/24 |
|
||||
| [KeyCloak](/recipes/keycloak/) | 172.16.49.0/24 |
|
||||
| [Duplicati](/recipes/duplicati/) | 172.16.55.0/24 |
|
||||
| [Restic](/recipes/restic/) | 172.16.56.0/24 |
|
||||
| [Paperless NG](/recipes/paperless-ng/) | 172.16.58.0/24 |
|
||||
|
||||
@@ -19,6 +19,7 @@ copyright: 'Copyright © 2016 - 2021 David Young, Funky Penguin Limited'
|
||||
|
||||
# Plugins
|
||||
plugins:
|
||||
# privacy:
|
||||
search:
|
||||
minify:
|
||||
minify_html: true
|
||||
|
||||
@@ -1,11 +1,22 @@
|
||||
mkdocs>=1.0.4
|
||||
pymdown-extensions>=6.0
|
||||
Markdown>=3.0.1
|
||||
mkdocs-minify-plugin>=0.2
|
||||
mkdocs-autolinks-plugin>=0.2.0
|
||||
# mkdocs-htmlproofer-plugin>=0.0.3
|
||||
mkdocs-git-revision-date-localized-plugin>=0.4.8
|
||||
mkdocs-macros-plugin
|
||||
mkdocs-material
|
||||
#mkdocs>=1.0.4
|
||||
#pymdown-extensions>=6.0
|
||||
#Markdown>=3.0.1
|
||||
#mkdocs-minify-plugin>=0.2
|
||||
#mkdocs-autolinks-plugin>=0.2.0
|
||||
## mkdocs-htmlproofer-plugin>=0.0.3
|
||||
#mkdocs-git-revision-date-localized-plugin>=0.4.8
|
||||
#mkdocs-macros-plugin
|
||||
#mkdocs-material
|
||||
|
||||
|
||||
# Direct dependencies
|
||||
jinja2>=3.0.2
|
||||
markdown>=3.2
|
||||
mkdocs>=1.3.0
|
||||
mkdocs-material-extensions>=1.0.3
|
||||
pygments>=2.12
|
||||
pymdown-extensions>=9.4
|
||||
|
||||
# My own dependencies
|
||||
mkdocs-git-committers-plugin-2
|
||||
mkdocs-meta-descriptions-plugin
|
||||
mkdocs-meta-descriptions-plugin
|
||||
|
||||
Reference in New Issue
Block a user